
Who doesn’t know about Disqus? It is the most commonly used hosted discussion system on news websites and forums. Of course, this requires subscribing to the service in order to comment. So, if you have an account on Disqus since 2007, then you have every reason to worry since the service became a victim of a targeted hack attack in 2012 where database from 2007 was hacked.
So far we had heard rumors about the hacking of Disqus, but the company remained mum on the issue. Finally, Disqus has confirmed that its web commenting system was indeed compromised in 2012. The company claims that unauthorized access hasn’t been detected as yet, but as a precautionary measure, users must reset their passwords.
“Yesterday, on October 5th, we were alerted to a security breach that impacted a database from 2012. While we are still investigating the incident, we believe that it is best to share what we know now. We are contacting all of the users whose information was included to inform them of the situation. Your trust in Disqus is important to us, and we’re working hard to maintain that.”
Reportedly, in the data breach that occurred in July 2012 hackers managed to steal Disqus’s database containing 17.5million email addresses. The breach, however, has been investigated recently by Disqus and currently it is performing the mandatory task of alerting users about the data hack.
According to the investigation conducted by Disqus, the database that was hacked had user records from the year 2007, and the attackers are yet unknown. They have provided a snapshot of the hacked database as well. The information stored in this database included email IDs, usernames, subscription dates and last login date. All the information was stored in plaintext format.
Since the passwords were hashed with the unreliable SHA1 algorithm at that time and Disqus switched to bcrypt in 2012. Therefore, it is believed that about a third of the total 17.5 million affected users might also have lost their passwords. Moreover, now these users are vulnerable to all sorts of phishing scams and spam messages. As the company noted itself:
“Email addresses are in plain text here, so it’s possible that affected users may receive spam or unwanted emails.”
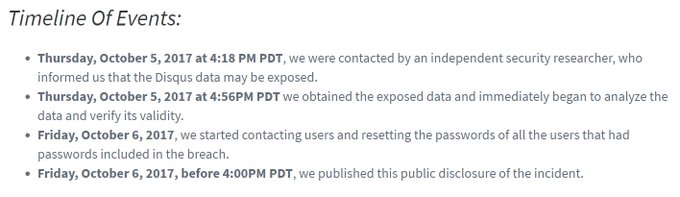
It must be noted that well-known security researcher Troy Hunt (owner of data breach notifying service Have I Been Pwned) informed Disqus about this data hack. Hunt Tweeted about his finding after he discovered a copy of the hacked database. He immediately informed Disqus and within 24 hours the company took necessary action of conducting an investigation and alerting the affected users, which highly impressed Hunt.
“In the space of less than 24 hours after first learning of the breach, Disqus has managed to assess the breach data, establish a timeline of events, reset passwords on impacted accounts, craft a very transparent announcement and liaise candidly with the press,” noted Hunt.
Hunt further stated that “It’s a gold standard for responding to a security incident and sets a very high bar for others to aspire to in future.”
The hacked database represents just 10% of the entire database of Disqus, and in the hacked database most of the accounts didn’t have passwords because users logged in through a third party service such as Google or Facebook. Therefore, the damage in that sense is not severe.
Disqus is the number one “blog comment hosting service” that is available for websites and online communities and the largest provider of web-based comments plugins on the web. It creates and provides comment plugins for news websites and therefore, it comes as no surprise that cybercriminals tried to attack this popular forum as well.
Thanks for sharing such a great blog Keep posting.
ResponderExcluircrm software
company database
sales automation
sales intelligence
CRM software
marketing intelligence
list of mnc companies in delhi ncr with contact details
hr contacts database
indian business directory database excel
Company Database India