by Waqason October 28th, 2021 in HackRead
CyberArk’s security researcher made a startling discovery while examining Wi-Fi networks in Tel Aviv, Israel. According to the researcher Ido Hoorvitch, 70% or around three-quarters of home and small-scale office Wi-Fi network passwords were vulnerable to hacking using inexpensive hacking tools.
Network Routers Hackable with Inexpensive Tools
Hoorvitch gathered a sample of 5,000 network hashes from across the city with Wi-Fi sniffing gear to use for this examination. He then identified that the attack could be launched using a laptop and a Wi-Fi signal extender, which cost no more than $50. Moreover, he claims that the full hacking setup can be fitted into a backpack.
Then, a signal booster is used to run scripts to exploit the vulnerabilities previously identified in the Robust Security Network Information Element (RSNIF), which allowed him to extract hashed Pairwise Master Key Identifier or PMKID network keys without intercepting the traffic.
SEE: This map shows free WiFi passwords from airports worldwide
Hence, he could crack the passwords of most of the network router passwords through Wi-Fi sniffing and open-source hacking tools. Some of the other tools Hoorvitch used to hack Wi-Fi network routers include packet capture tools and hardware drivers that enable monitor mode when synced with the signal extender.
How The Hack Works?
Using the Wi-Fi sniffing setup, the researcher picked up hashed passwords for sampling while wandering across Tel Aviv metropolitan area. According to Hoorvitch, just this area houses over 3.9 million residents, and this indicates the high number of vulnerable devices.
“You can imagine what the numbers would have been had we not cut our research off at 5,000 Wi-Fi networks. And while this research was conducted in Tel Aviv, the routers that were susceptible to this attack — from many of the world’s largest vendors — are used by households and businesses worldwide,” he explained in a blog post.
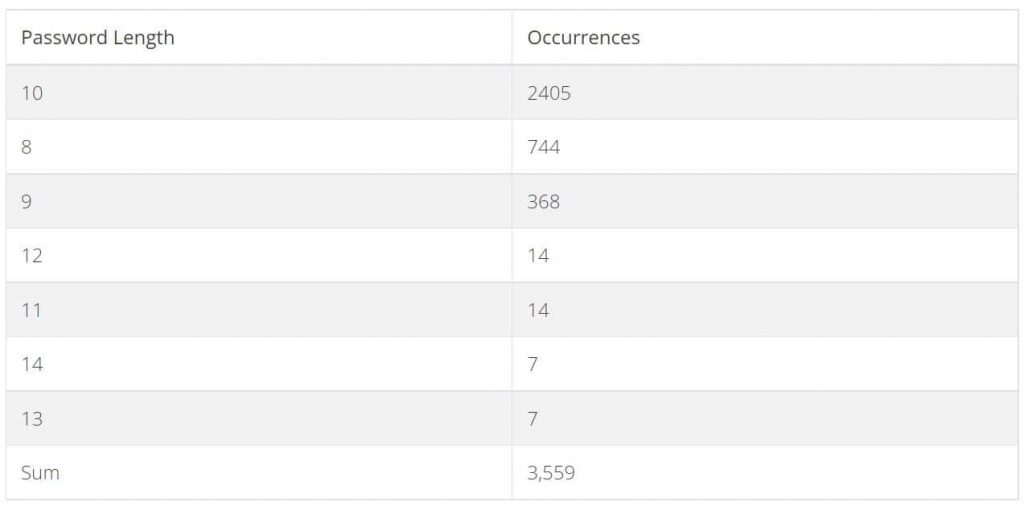
Then the process of decoding the passwords began, which was an easy feat to accomplish since Israeli networks use the owner’s mobile phone number as the router’s password. He passed the hashed passwords with the Hashcat tool and could crack 2,200 passcodes out of 5,000.
SEE: Tesla cars can be remotely hacked using drone, WIFI dongle
Another pass allowed him to crack more passcodes, and by the end of the research, Hoorvitch had obtained around 3,559 valid passcodes out of 5,000 sniffed samples.
However, he discovered a problem with this attack method- that it worked only when Wi-Fi roaming was enabled on the targeted routers, and not all routers supported this feature. So, such routers weren’t susceptible to the PMKID attack.
“However, our research found that routers manufactured by many of the world’s largest vendors are vulnerable,” the researcher concluded.
How to Protect your Network Against PMKID Attack?
If you want to protect your networks, Hoorvitch suggests following best practices like using a lengthy and complex password and regularly updating the default login settings. In addition to this, you must update router firmware, turn off Wi-Fi Protected Setup, and disable WAP1 and WAP (Wi-Fi Application Protocol) specifications.
“The bottom line is that in a couple of hours and with approximately $50, your neighbor or a malicious actor can compromise your privacy and much more if you don’t have a strong password.”