Por Wagas em 06/12/2017 no site HackRead

There are over one billion devices with TeamViewer, a software that allows users to conduct online meetings, desktop sharing, remote control, file transfer, etc. between computers. So when there is a vulnerability in such a widely used program, it becomes a big thing.
Recently, a GitHub user going by the online handle of “Gellin” discovered a critical vulnerability in TeamViewer that allows an attacker or client to remotely take over a computer without consent or knowledge of its owner.
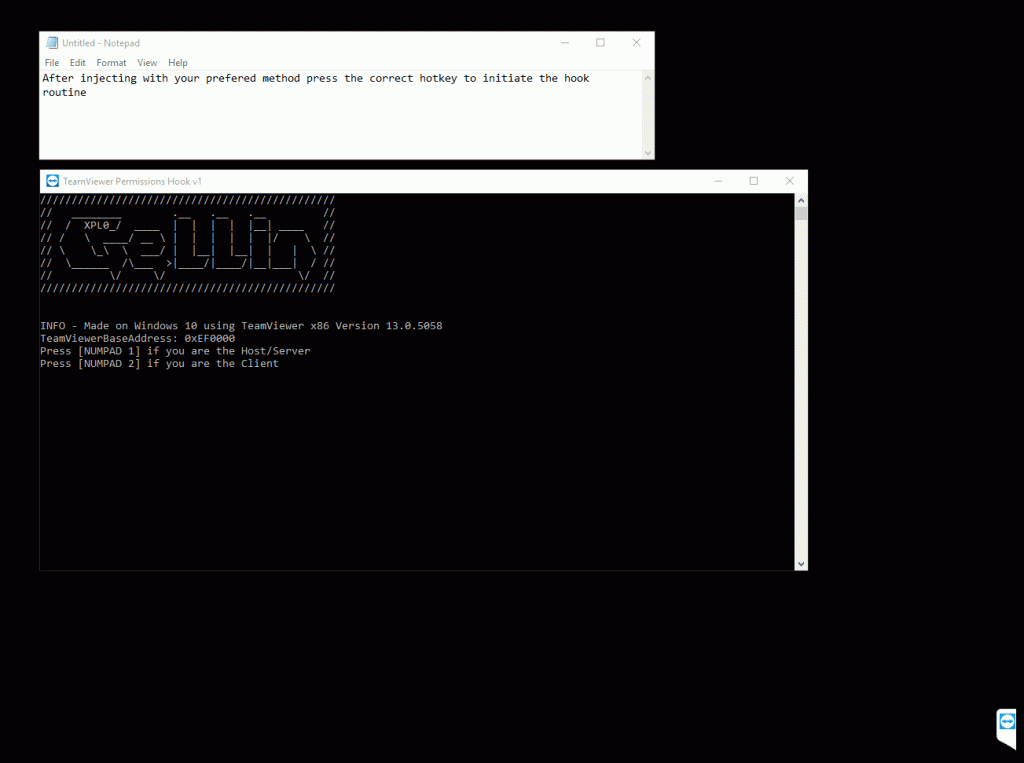
According to proof-of-concept (PoC) published on GitHub, “an injectable C++ dll, which uses naked inline hooking and direct memory modification to change your TeamViewer permissions.” That means victim remains uninformed once TeamViewer permissions are modified.
Gellin tested the vulnerability on TeamViewer x86 Version 13.0.5058 and it transpired that it can be exploited to enable the “switch sides” feature which an attacker can use to take control of victim’s PC during the desktop session. By default, only a client can manually allow another user to access their device through TeamViewer however the vulnerability also grants user control over mouse and control settings and permissions.
“Exploited as a presenter you are able to turn on a ‘switch sides’ feature (that usually needs the client to agree to) and change controls and sides, controlling a viewer’s computer. If exploited as a viewer, you are able to control the mouse of the presenter’s computer no matter what settings or permissions the presenter may have had set,” TJ Nelson, a security researcher with Arbor Networks told ThreatPost.
The vulnerability affects TeamViewer on macOS, Linux, and Windows systems while a patch for Linux and macOS versions of TeamViewer will be out Tuesday or Wednesday while a patch for Windows was already issued on Tuesday.
According to Axel Schmidt, senior PR manager for TeamViewer, users who have automatic update enable will get the update automatically but those who don’t will be notified once the update is available.
Nenhum comentário:
Postar um comentário