Swati Khandelwal
Em 14/09/2017 no site The Hacker News
Even after so many efforts by Google, malicious apps somehow managed to fool its Play Store's anti-malware protections and infect people with malicious software.
The same happened once again when at least 50 apps managed to make its way onto Google Play Store and were successfully downloaded as many as 4.2 million times—one of the biggest malware outbreaks.
Security firm Check Point on Thursday published a
blog post revealing at least 50 Android apps that were free to download on official Play Store and were downloaded between 1 million and 4.2 million times before Google removed them.
These Android apps come with hidden malware payload that secretly registers victims for paid online services, sends fraudulent premium text messages from victims' smartphones and leaves them to pay the bill—all without the knowledge or permission of users.
Dubbed
ExpensiveWall by Check Point researchers because it was found in the Lovely Wallpaper app, the malware comes hidden in free wallpaper, video or photo editing apps. It's a new variant of malware that Mcafee
spotted earlier this year on the Play Store.
But what makes ExpensiveWall malware different from its other variants is that it makes use of an advanced obfuscation technique called "packed," which compresses malicious code and encrypts it to evade Google Play Store's built-in anti-malware protections.
The researchers notified Google of the malicious apps on August 7, and the software giant quickly removed all of them, but within few days, the malware re-emerged on the Play Store and infected over 5,000 devices before it was removed four days later, Check Point said.
Here's How ExpensiveWall Malware Works:
Once an app with ExpensiveWall—which researchers think came from a software development kit called GTK—is downloaded on a victim's device, the malicious app asks for user's permission to access the Internet, and send and receive SMS messages.
The internet access is used by the malware to connect the victim's device to the attacker's command and control server, where it sends information on the infected handset, including its location alongside unique hardware identifiers, such as MAC and IP addresses, IMSI and IMEI numbers.
The C&C server then sends the malware a URL, which it opens in an embedded WebView window to download JavaScript code that begins to clock up bills for the victim by sending fraudulent premium SMS messages without their knowledge, and uses the victim's phone number to register for paid services.
However, according to the Check Point researchers, it is still unclear how much revenue was generated via ExpensiveWall's premium SMS scam.
Google's Play Store—Home for Malware
Android malware continues to evolve with more sophisticated and never-seen-before capabilities with every passing day, and spotting them on Google Play Store has become quite a common thing.
Last month, over
500 Android apps with spyware capabilities were found on Play Store, which had been downloaded more than 100 million times.
In July,
Lipizzan spyware apps were spotted on Play Store that can steal a whole lot of information on users, including text messages, emails, voice calls, photos, location data, and other files, and spy on them.
In June, more than
800 Xavier-laden apps were discovered on Google Play that had been downloaded millions of times, and the same month researchers found first
code injecting rooting malware making rounds on Google Play Store.
A month prior to it, researchers spotted 41 apps on Play Store hidden with the
Judy Malware that infected 36.5 million Android devices with malicious ad-click software.
In April, over
40 apps with hidden FalseGuide malware were spotted on Play Store that made 2 Million Android users victims.
Earlier this year, researchers also discovered a new variant of the
HummingBad malware, dubbed
HummingWhale, hidden in more than 20 apps on Google Play Store, which were downloaded by over 12 Million users.
How to Protect Your Android From Such Malware Apps
Even after Google removed all the malware-tainted apps from its official Play Store marketplace, your smartphones will remain infected with the ExpensiveWall malware until you explicitly uninstall the malicious apps, if you have downloaded any.
Google has recently provided a security feature known as
Play Protect that uses machine learning and app usage analysis to automatically remove malicious apps from the affected smartphones to prevent further harm.
However, according to the Check Point researchers, many phones run an older version of Android that does not support the feature, leaving a wide audience open to malware attacks.
You are strongly advised to always keep a good antivirus app on your device that can detect and block any malicious app before it can infect your device, and always keep your device and all apps up-to-date.
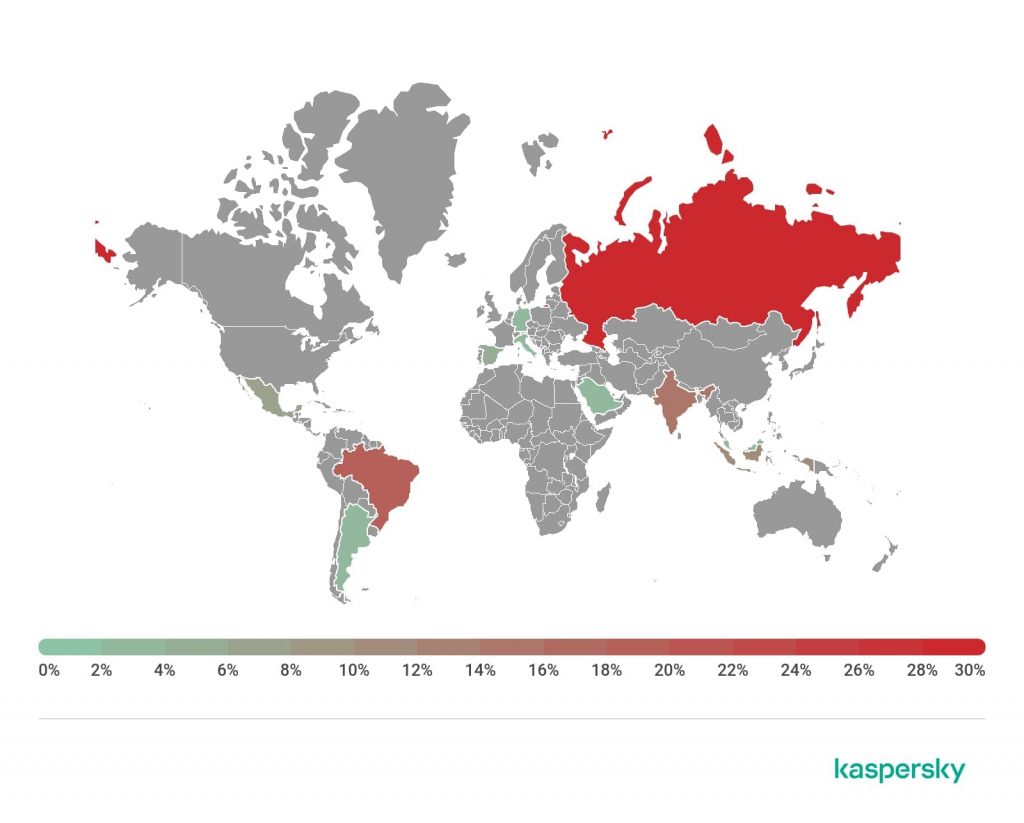 Currently, (as shown above) with the statistics released by researchers, it was revealed that it is the most widespread in Russia with 28.46% of infected users. Brazil and India conveniently follow at 18.70% and 14.23% respectively.
Currently, (as shown above) with the statistics released by researchers, it was revealed that it is the most widespread in Russia with 28.46% of infected users. Brazil and India conveniently follow at 18.70% and 14.23% respectively. Currently, (as shown above) with the statistics released by researchers, it was revealed that it is the most widespread in Russia with 28.46% of infected users. Brazil and India conveniently follow at 18.70% and 14.23% respectively.
Currently, (as shown above) with the statistics released by researchers, it was revealed that it is the most widespread in Russia with 28.46% of infected users. Brazil and India conveniently follow at 18.70% and 14.23% respectively.

