“Archive Poster” extension for Chrome browser is being currently used by 105,000 users. The primary function of this extension is to allow users to “quickly reblog, queue, draft, and like posts right from another blog’s archive” but now, a Las Vegas-based security researcher Troy Mursch (“Bad Packets” on Twitter) has identified that Archive Poster is infecting user browser with a cryptocurrency miner.
Generating Monero Through CoinHive
According to Bad Packets’ analysis, the malicious Chrome extension is using cryptocurrency mining code provided by CoinHive and uses victim’s computer power to generate Monero (XMR) digital coin (1 XMR equals $392.71 USD). CoinHive is a company that provides cryptocurrency miner, which sends any coins mined by the browser to the owner of the website, application or extension.
In the case of Archive Poster, a number of users reviewed that the extension tries to use their browser for mining purposes. One of the reviews posted on December 8th, 2017, by Furkan Tunalı said “I rated it 5 before. Now it’s mining with your CPU by CoinHive in the background. Beware Sad.”
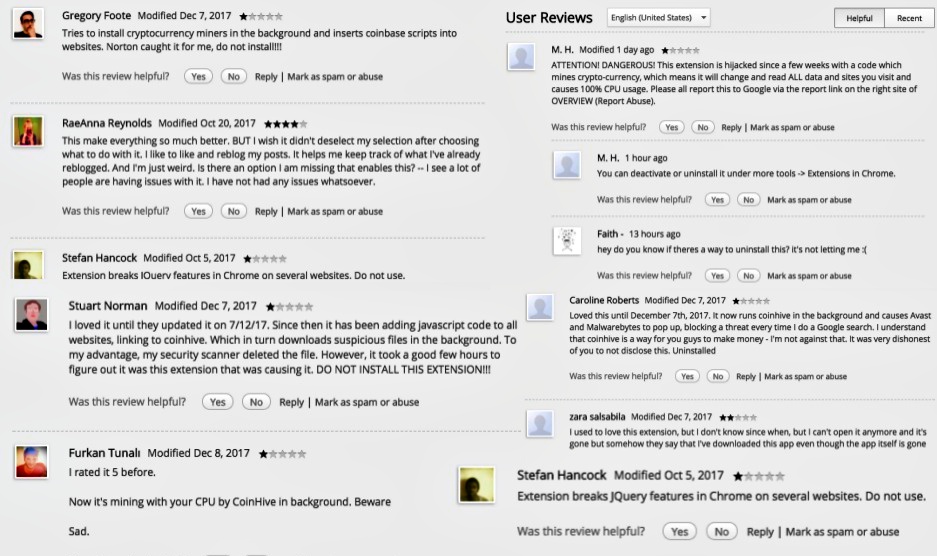
In a Twitter thread, Bad Packets stated that CoinHive’s JavaScript code loads from this URL: https://c7e935.netlify[.]com/b.js
Extension Is Up And Running
Mursch told HackRead that they reported the issue to Google but there was no response from the company. Another user who reported the presence of cryptocurrency miner extension received the following reply that did not make sense.
Remember, a couple of weeks ago, HackRead identified a malware scam in which hackers used Google AdWords and Google Sites to drop malware in fake Chrome browser downloader file. The issue was reported to Google, however, there was no reply from the company.
Mursch is urging users to report “Archive Poster” extension to Google but maintains that it might be work of a “disgruntled employee.”
Monero Mining On Facebook And Android Phones
Monero mining is not limited to PCs, extensions or websites. In fact, hackers are infecting Android apps with Monero code to use Android devices to generate Monero coins. Furthermore, Facebook users on Messenger are also at risk of being infected with Monero mining Malware called Digmine.
How To Stop CoinHive Code From Using Your CPU Power
In October this year, Google announced blocking cryprocurrency miners with new security features in Chrome, but, Opera browser was quick to understand the seriousness of the matter and introduced Opera 50 beta version that comes with a builtin cryptocurrency Mining Blocker.
Since the use of the CoinHive code is increasing, there are several ways to block the code from using your computer. For instance, No Coin and minerBlock extensions available on Chrome web store are developed to block any crypto miners from using your computing power.
At the time of publishing this article, Archive Poster extension was still available on Chrome Web Store.