by Christopher Kanaracus em 05/02/2018 no site Threatpost
A new botnet that distributes malware for mining Monero cryptocurrency has emerged, infecting Android devices through a port linked with a debugging tool for the OS, according to researchers at Qihoo 360 Netlab.
Dubbed ADB.Miner by 360 Netlab, the botnet is gaining entry to Android devices–mostly smartphones and TV boxes–through port 5555, which is associated with Android Debug Bridge, a command-line tool that is used for debugging, installing apps and other purposes.
ADB typically communicates with devices via USB, but it’s also possible for it to use wifi with some setup, according to Android documentation.The botnet propagates itself in “worm”-like fashion, looking for open 5555 ports on other devices, most of which are Android-based, 360 Netlab researcher Hui Wang said in a blog post.
Notably, it uses some port scanning code from the Mirai botnet, which is the first time Mirai code has been used to target Android devices, he claimed. Mirai, which emerged in August 2016, has historically been used to attack Linux devices.
Most of the Android devices being targeted by ADB.Miner are located in China and South Korea, but 360 Netlab is not identifying any of them at this time.
“Overall, we think there is a new and active worm targeting android system’s adb debug interface spreading, and this worm has probably infected more than 5,000 devices in just 24 hours,” Wang wrote. In fact, 5555 port scanning traffic has hit the top 10, according to 360 Netlab’s own scanning data.
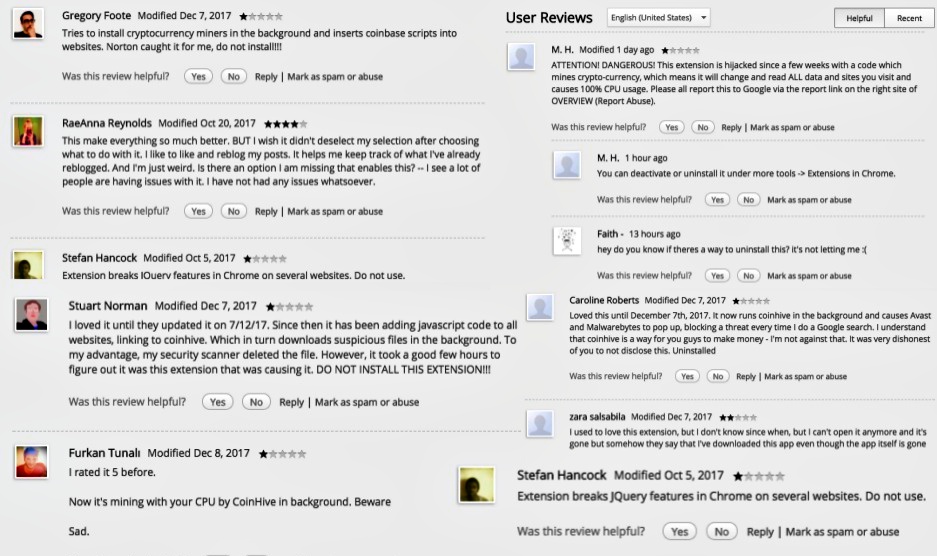
The botnet is distributing malicious code that is mining Monero coins, but as of yet none have been paid out, according to Wang.
Cybercriminals have been increasingly turning to cryptocurrency mining via botnets, with Monero a favored target. Those behind the massive Smominru botnet have generated as much as $3.6 million since May through an army of more than 500,000 infected machines, according to Proofpoint.
Crypto mining botnets have clear advantages over other types of attacks, such as ransomware, since they don’t necessarily require social engineering and by their nature are meant to operate stealthily, stealing nothing from victims but CPU cycles. In fact, crypto miners may be the “new payload of choice” for cybercriminals, researchers at Cisco Talos said recently.