This malware disables Google’s only security mechanism against malware-infected apps on the Play Store.
While the Android and iOS fanbase can be found constantly at war over the advantages one offers as compared to the other, there is one place where iOS wins by miles. We are talking about security with the latest malware discovered by Kaspersky Lab among an app on the Play Store.
Dubbed “Trojan-Dropper.AndroidOS.Shopper.a,” the trojan tricks users into being downloaded by posing with a system icon and a similar name to a legitimate Android application. Once the fish (YOU) takes the bait, it starts with its magic by collecting your device’s sensitive and not-so-sensitive information including the IMEI Number, IMSI number, the network type and the country it is in.
Once done, it sends the data to its command & control server (C&C) from which attackers behind the campaign can coordinate their future moves. These include tasks such as “Opening links received from the remote server in an invisible window (whereby the malware verifies that the user is connected to a mobile network)” as detailed by researchers.
But this isn’t where it ends. Additionally, the trojan helps boost the popularity of other “sister-malicious-apps” on the Play Store by posting overly optimistic reviews. Leaving the user little to do, it also happens to install certain apps from a third party store named Apkpure[.]com with the victim’s permission.
How it does this is by abusing an accessibility service present to facilitate the disabled. To prevent any detection, it also disables the “Google Play Protect” which is normally used to protect Android users from such malware.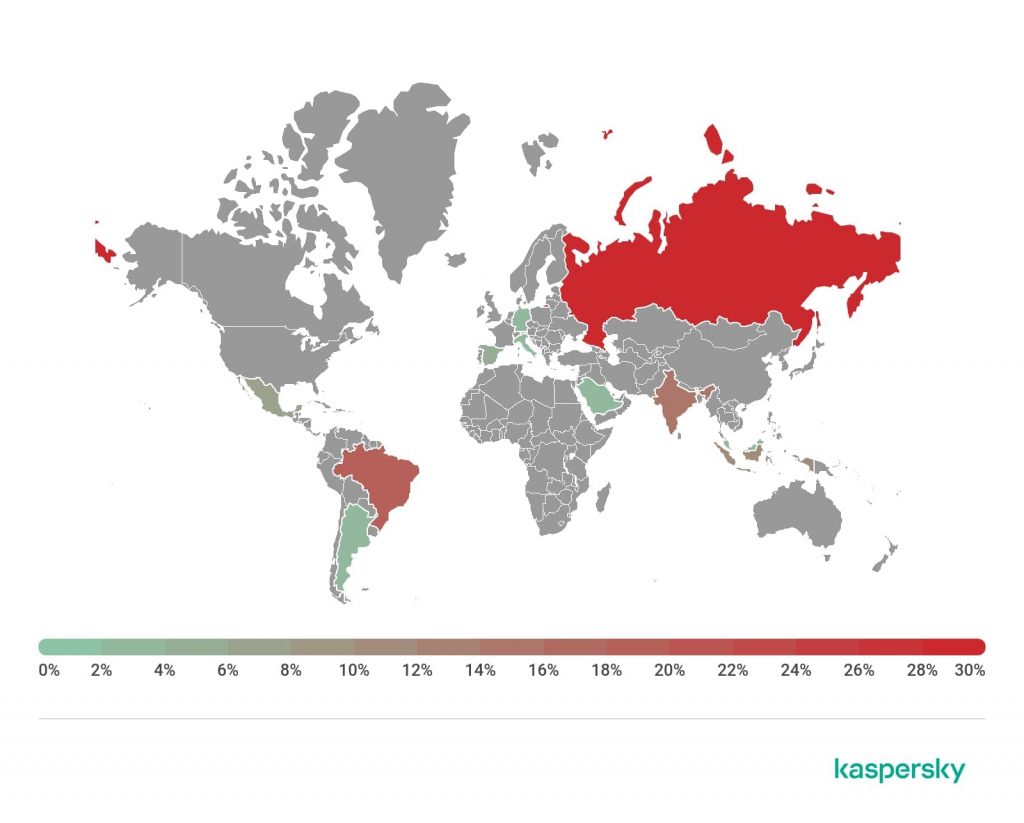 Currently, (as shown above) with the statistics released by researchers, it was revealed that it is the most widespread in Russia with 28.46% of infected users. Brazil and India conveniently follow at 18.70% and 14.23% respectively.
Currently, (as shown above) with the statistics released by researchers, it was revealed that it is the most widespread in Russia with 28.46% of infected users. Brazil and India conveniently follow at 18.70% and 14.23% respectively.
 Currently, (as shown above) with the statistics released by researchers, it was revealed that it is the most widespread in Russia with 28.46% of infected users. Brazil and India conveniently follow at 18.70% and 14.23% respectively.
Currently, (as shown above) with the statistics released by researchers, it was revealed that it is the most widespread in Russia with 28.46% of infected users. Brazil and India conveniently follow at 18.70% and 14.23% respectively.
