Swati Khandelwal em 29/01/2018
More than 2,000 WordPress websites have once again been found infected with a piece of crypto-mining malware that not only steals the resources of visitors' computers to mine digital currencies but also logs visitors' every keystroke.
Security researchers at Sucuri discovered a malicious campaign that infects WordPress websites with a malicious script that delivers an in-browser cryptocurrency miner from CoinHive and a keylogger.
Coinhive is a popular browser-based service that offers website owners to embed a JavaScript to utilise CPUs power of their website visitors in an effort to mine the Monero cryptocurrency.
Sucuri researchers said the threat actors behind this new campaign is the same one who infected more than 5,400 Wordpress websites last month since both campaigns used keylogger/cryptocurrency malware called cloudflare[.]solutions.
Spotted in April last year, Cloudflare[.]solutions is cryptocurrency mining malware and is not at all related to network management and cybersecurity firm Cloudflare. Since the malware used the cloudflare[.]solutions domain to initially spread the malware, it has been given this name.
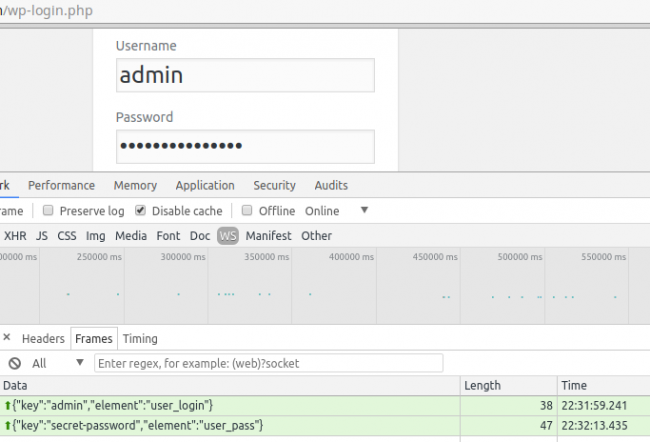
The malware was updated in November to include a keylogger. The keylogger behaves the same way as in previous campaigns and can steal both the site's administrator login page and the website's public facing frontend.
If the infected WordPress site is an e-commerce platform, hackers can steal much more valuable data, including payment card data. If hackers manage to steal the admin credentials, they can just log into the site without relying upon a flaw to break into the site.
The cloudflare[.]solutions domain was taken down last month, but criminals behind the campaign registered new domains to host their malicious scripts that are eventually loaded onto WordPress sites.
The new web domains registered by hackers include cdjs[.]online (registered on December 8th), cdns[.]ws (on December 9th), and msdns[.]online (on December 16th).
Just like in the previous cloudflare[.]solutions campaign, the cdjs[.]online script is injected into either a WordPress database or the theme's functions.php file. The cdns[.]ws and msdns[.]online scripts are also found injected into the theme's functions.php file.
The number of infected sites for cdns[.]ws domain include some 129 websites, and 103 websites for cdjs[.]online, according to source-code search engine PublicWWW, though over a thousand sites were reported to have been infected by the msdns[.]online domain.
Researchers said it's likely that the majority of the websites have not been indexed yet.
"While these new attacks do not yet appear to be as massive as the original Cloudflare[.]solutions campaign, the reinfection rate shows that there are still many sites that have failed to properly protect themselves after the original infection. It’s possible that some of these websites didn't even notice the original infection," Sucuri researchers concluded.
If your website has already been compromised with this infection, you will require to remove the malicious code from theme's functions.php and scan wp_posts table for any possible injection.
Users are advised to change all WordPress passwords and update all server software including third-party themes and plugins just to be on the safer side.