Zoom video conferencing tool has been facing security and vulnerability issues since the beginning of the Coronavirus pandemic but this time Microsoft’s very own Microsoft Teams service was exposed to account take over vulnerability.
Microsoft Teams is a workplace collaboration and communication platform that allows organizations to communicate via video conferencing, store files, initiate chat, and integrate applications simultaneously. It has emerged as a very useful and productive medium of communication in recent times, specifically nowadays when the world is held hostage to the COVID-19 pandemic.
However, this very aspect is in itself a great threat to organizational data safety as none of the applications currently available are free from security loopholes, and the same is the case with Microsoft Teams.
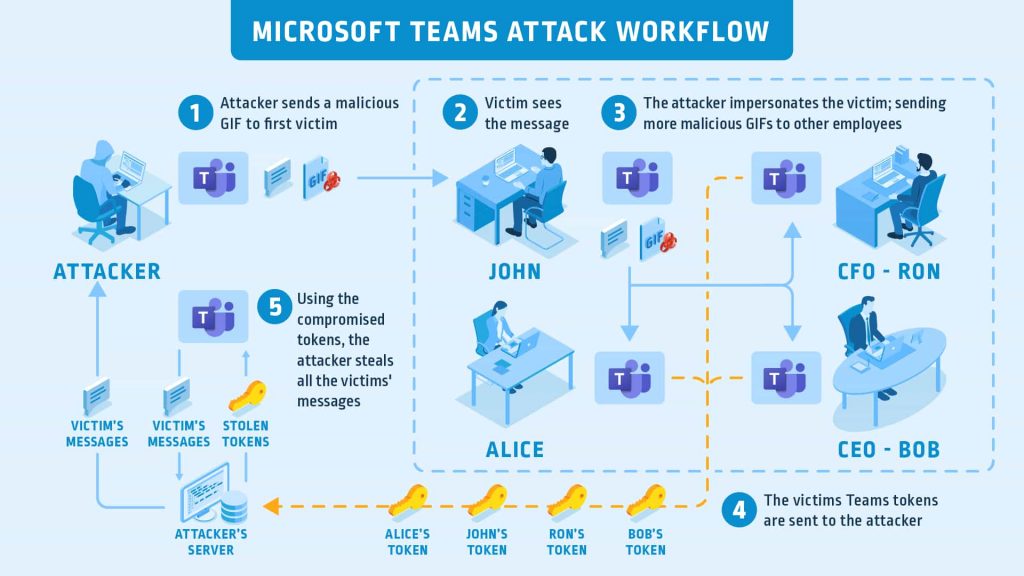
Reportedly, CyberArk’s researchers identified a worm-like vulnerability in Microsoft Teams, which hackers could exploit to hijack an entire roaster of MS Teams accounts at an organization by sending malicious URLs or GIF images to Teams users.
The vulnerability is related to the way MS Teams processes authentication access tokens and passes them to resources containing images. If an attacker manages to create a GIF file or URL, Teams will send the authentication token to the attacker’s server while processing it.
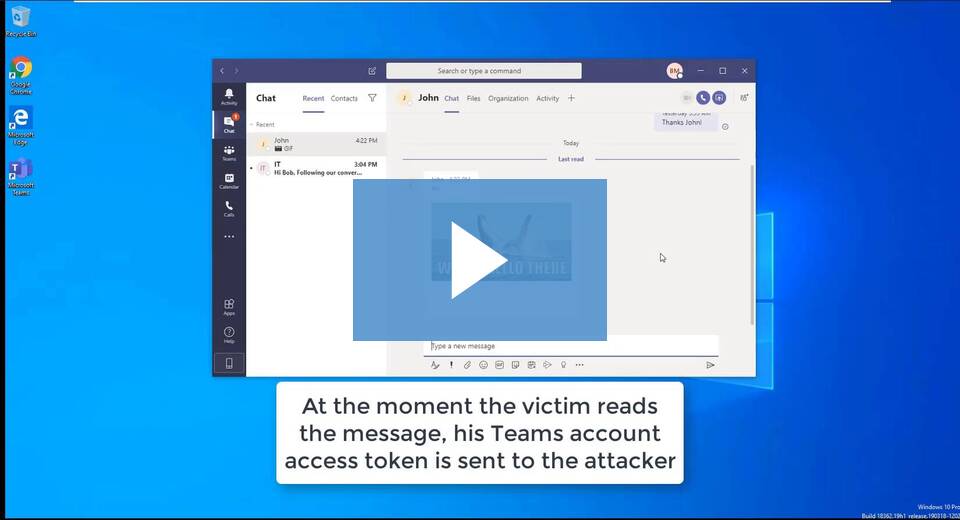
To successfully pull off the attack via sending links, the victim should click on the link; but in the case of GIF image, the attack can be successful if the user views the image in Teams chat. Once the image is viewed or URL clicked, the attacker receives the token.
Using this token, an attacker can hijack the victim’s Teams account by exploiting its API interfaces, and can access victim’s data on Teams, send messages, create and delete groups on the victim’s behalf, or modify a group’s permissions.
The automated nature of this attack makes organizations most vulnerable to exploitation as the attacker can send malicious GIF files to other employees using a hijacked account, and may access sensitive data, login credentials, business strategies/plans, and meeting schedules.
Attack’s workflow:
CyberArk researchers’ assessed that an attacker can carry out a variety of attacks after receiving the token. Such as:
It is possible to send false information to employees to cause reputational or financial damage, direct data leakage, install malware, lure an employee to reset the password by impersonating as a team member, or contact the CEO after hijacking Teams account of another executive to obtain confidential financial data.
However, they believe that sending out infected images or links is quite easy but the other steps are rather complex, and novice or amateur hackers cannot easily pull it off.
Watch how it’s done:
Microsoft has already addressed the flaw with the help of researchers under CVD (Coordinated Vulnerability Disclosure). The company claims that the vulnerability wasn’t yet exploited by hackers, and now that it has been fixed, there is no threat to the users of Microsoft Teams.
![<script async src="//pagead2.googlesyndication.com/pagead/js/adsbygoogle.js"></script>
<!-- Custom size sqare ad -->
<ins class="adsbygoogle"
style="display:inline-block;width:300px;height:250px"
data-ad-client="ca-pub-3675825324474978"
data-ad-slot="3421156210"></ins>
<script>
(adsbygoogle = window.adsbygoogle || []).push({});
</script> <script async src="//pagead2.googlesyndication.com/pagead/js/adsbygoogle.js"></script>
<!-- Text Link Ad -->
<ins class="adsbygoogle"
style="display:inline-block;width:200px;height:90px"
data-ad-client="ca-pub-3675825324474978"
data-ad-slot="5266209419"></ins>
<script>
(adsbygoogle = window.adsbygoogle || []).push({});
</script> <script async src="//pagead2.googlesyndication.com/pagead/js/adsbygoogle.js"></script>
<!-- Text Link Ad -->
<ins class="adsbygoogle"
style="display:inline-block;width:200px;height:90px"
data-ad-client="ca-pub-3675825324474978"
data-ad-slot="5266209419"></ins>
<script>
(adsbygoogle = window.adsbygoogle || []).push({});
</script>](https://www.hackread.com/wp-content/uploads/2020/04/vulnerability-hijacking-microsoft-teams-account-gif-2.jpg)